You might remember my previous post about a new Twitter worm called "m28sx" that spreads a fake antivirus (aka rogueware) called Security Shield:
Today I got an email with the subject "HELLoo" and only a link in it. The link ended with m28sx.html.
Different redirects starting at the compromised website
There are 3 redirects before you eventually land on the fake scanner page:
Messagebox alerting you of infections on your system
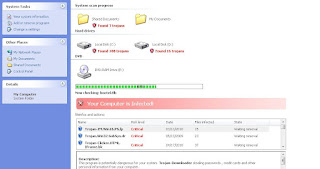
Fake scan message showing numerous infections
The following file is dropped:
pack.exe
Result: 7/43 (16.3%)
MD5: b7fcca77d20fb5ac43792ad56f6fc75e
The payload is a rogueware called 'Security Shield'.
When executing the dropped file (pack.exe) :
A warning that Security Shield was installed successfully
Security Shield rogueware finding (non-existant) infections
Conclusion
Always be careful when clicking on a URL that you do not recognize or is shortened so you cannot see the real URL. In this case, a website was compromised and the "m28sx.html" was placed. Actually, be careful with ANY URL ;) .
If you do happen to land on one of these rogueware pages presenting you a fake scan of your disks, open Task Manager and end your browser's process.
As an extra note: this one might re-surface again on Twitter, so be on the lookout these days for links that end with "m28sx".








No comments:
Post a Comment